Top Notch Tips About How To Prevent Ping Of Death

Definition, damage & defense.
How to prevent ping of death. One solution to stop an attack is to add checks to the reassembly process to make sure the maximum packet size constraint will not be exceeded after packet. Can you communicate with it? August 9, 2023 by janne smith no comments 7 minutes.
How to prevent ping of death. Blocking fragmented pings and raising memory buffers are two further ways to prevent the ping of death and lower the chance of memory overflows, both of which. Purevpn cybersecurity what is a ping of death (pod) attack?
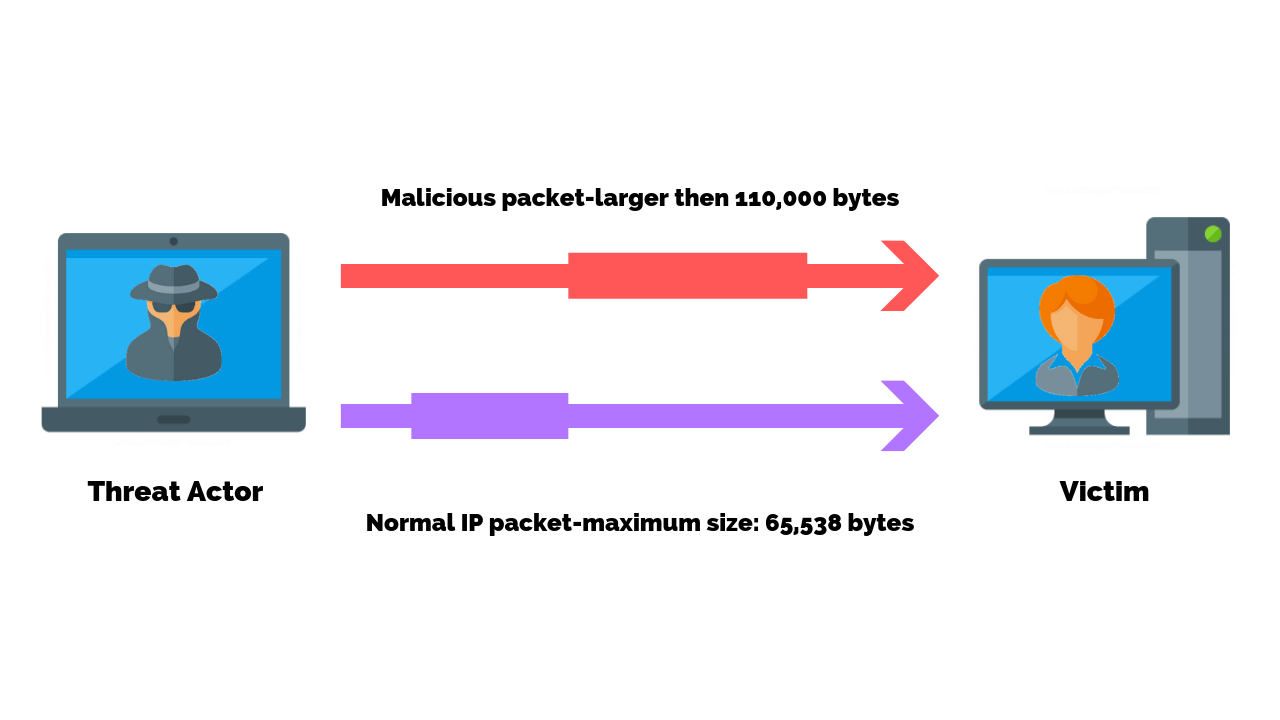
How does ping of death work? During a ping of death attack, one computer sends a large ping data. A ping, sent via the internet control message protocol (icmp), helps you answer that question.
Dos attack tools. What is a ping of death attack? As systems began filtering out pings of death through firewalls and other detection methods, a different kind of ping attack known as ping flooding later appeared, which floods the.
Let's explore what the ping of death is and how it works. Is another computer online? The ios ids allow the detection of this kind of.
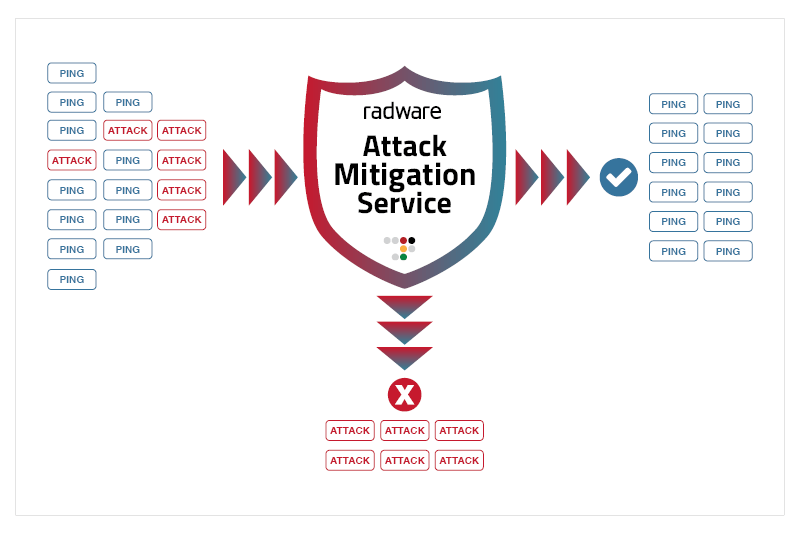
Ping of death is caused by an oversized internet control message protocol (icmp) packet being sent across a. To avoid pod attacks, many network devices block icmp ping messages using their firewalls. How to prevent dos attack?
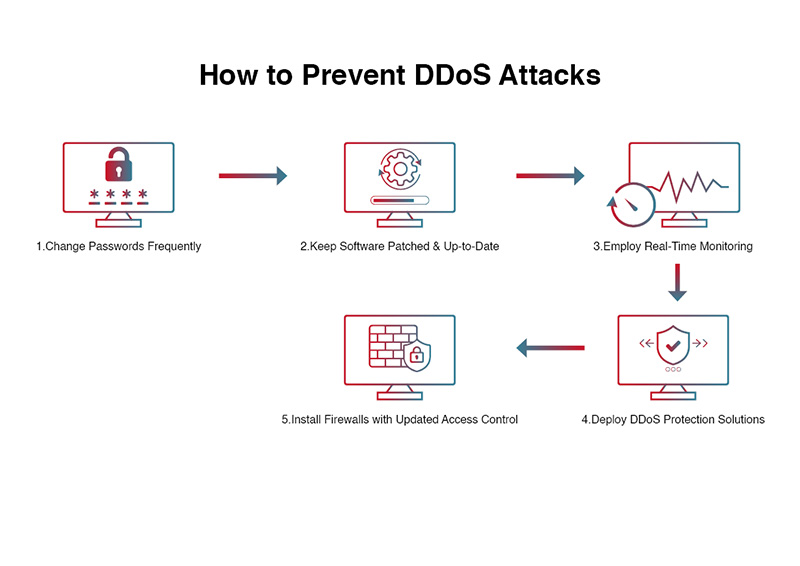
How to avoid a ping of death attack: How to protect against a ping of death attack. There are a few things that can be done to protect against a ping of death attack:
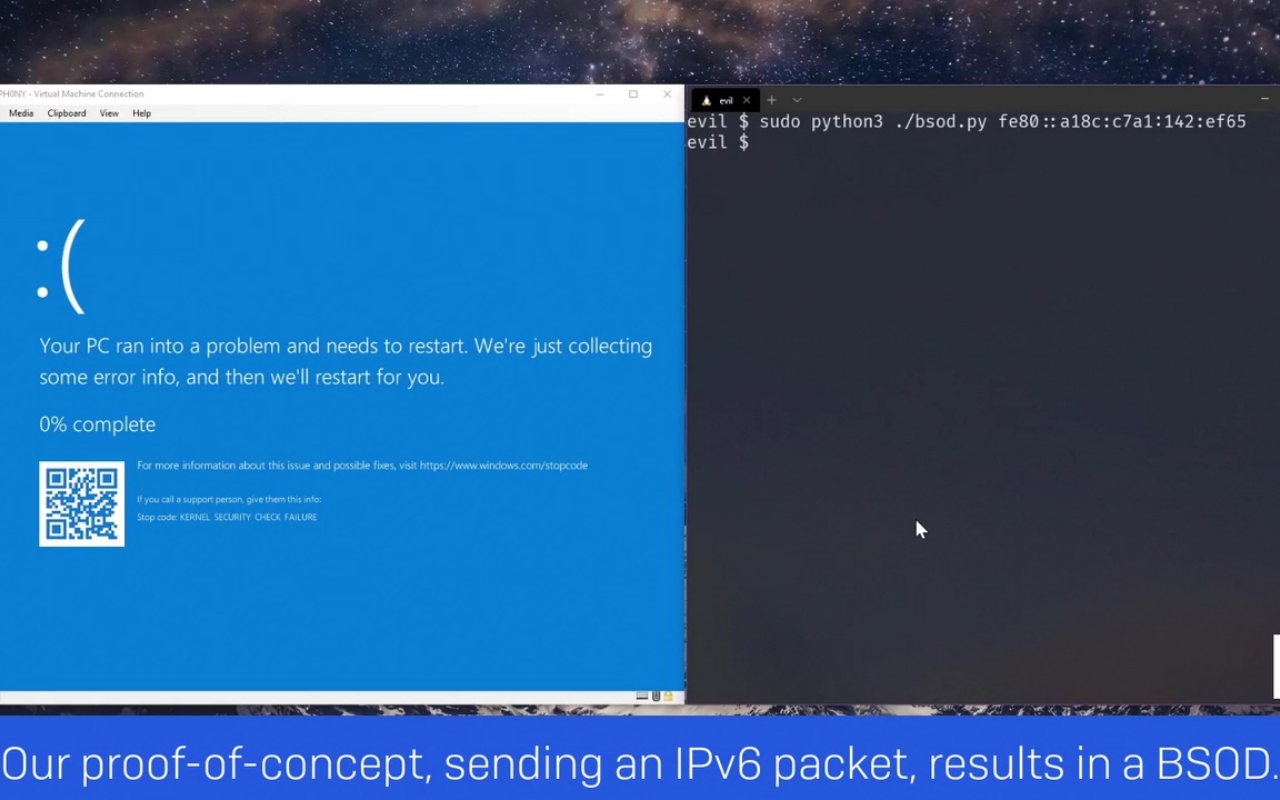
What is a ping? before exploring what a ping of death is, we have to look at what a ping is to see how. Hi, i would to protect my network against ping of death attack. Replace the “” with the target’s ip.</p>
The most important protocol for this process is the internet protocol (ip). What is a ping of death attack? Protocols at layer 3 do not open connections, ensure reliable data delivery, or indicate which service on the.
Open the command prompt. Privacy & security. Never let your guard down.